Ransomware attacks are a growing threat facing businesses of all sizes and in every industry. These attacks aren’t just happening more often; they’re becoming more expensive. Learn more about the high cost of ransomware attacks and what your business needs to do to be protected from Tolar Systems.
Ransomware attacks are a growing threat facing businesses of all sizes, in every industry. As we discussed in our first article in this series, ransomware attacks are happening with greater frequency. But it’s not just the fact that these attacks are happening more frequently that should give business owners and executives pause. It’s also the fact that these attacks are becoming more expensive.
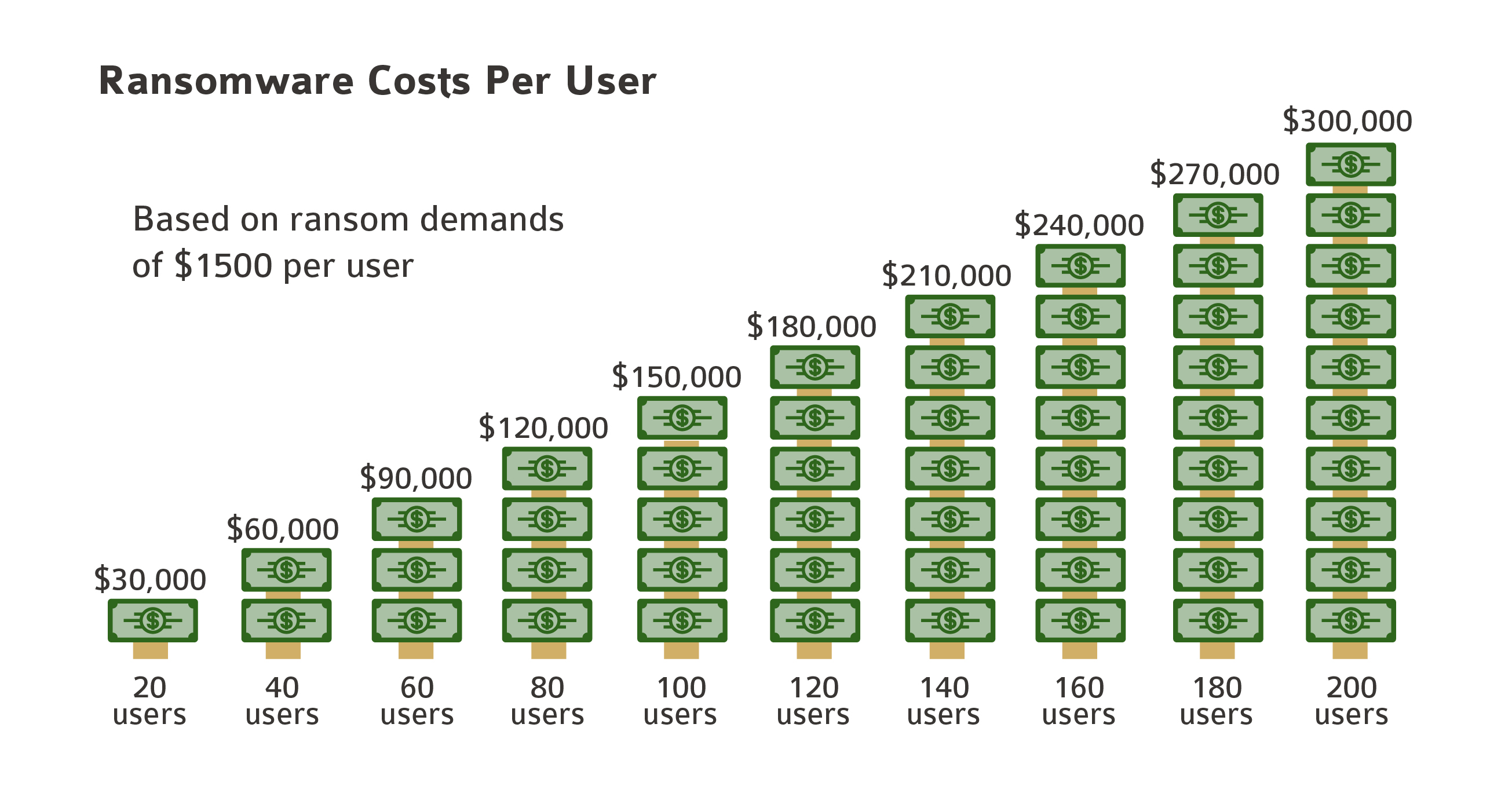
Ransom demands are growing, with ransoms typically demanding sums between $500 to $2500 to release an individual user’s data. Some ransom demands can be as high as $5,000 per user to regain access to your data. For an organization with 20 users, that could result in a cost as high as $50,000 to even $100,000 to access your own data.
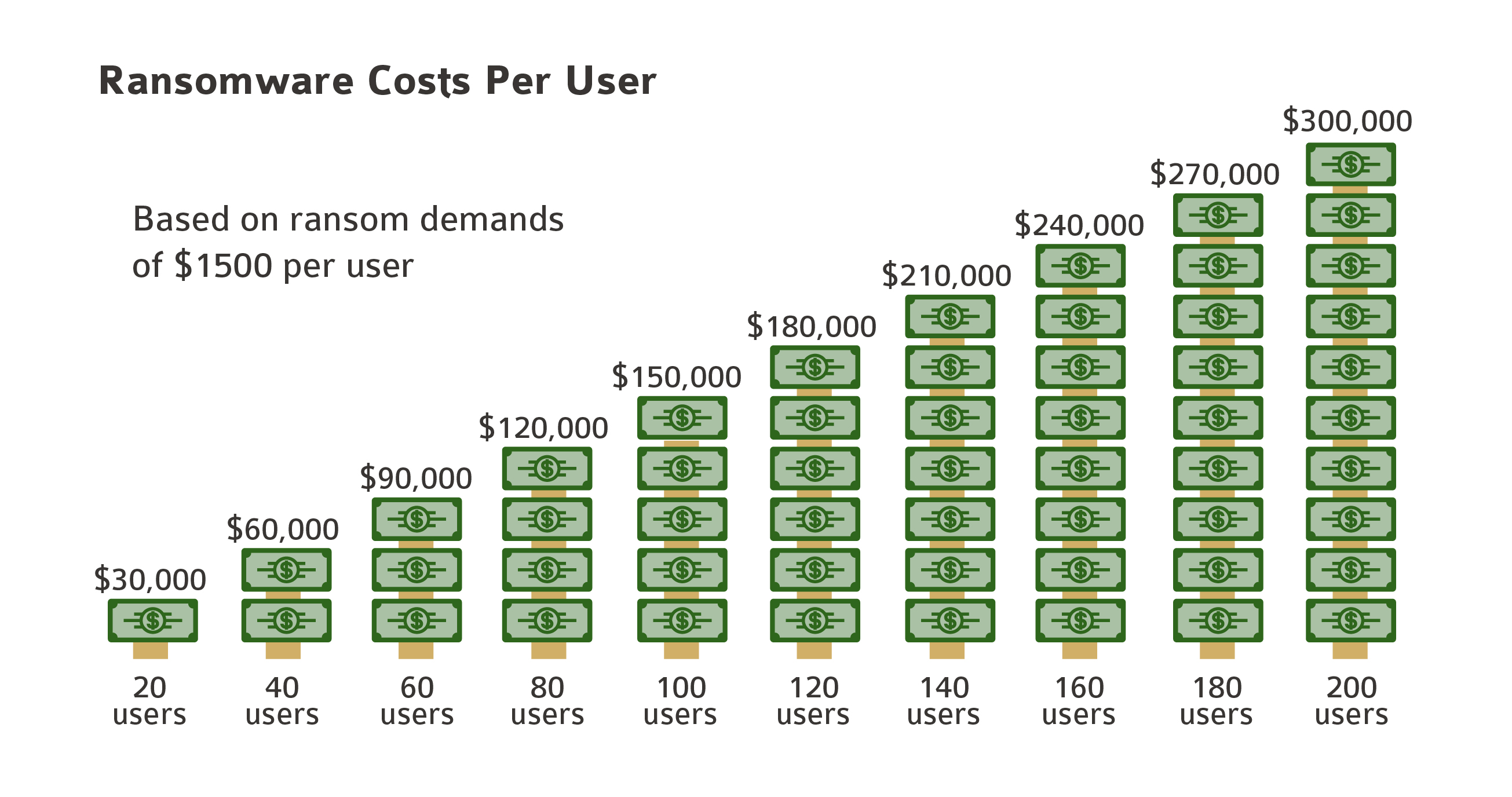
According to another recent survey of mid-size businesses, the average cost of a ransomware attack was $133,000, with more than 5 percent of the organizations surveyed reporting costs that exceeded 1 million dollars, often over several attacks.
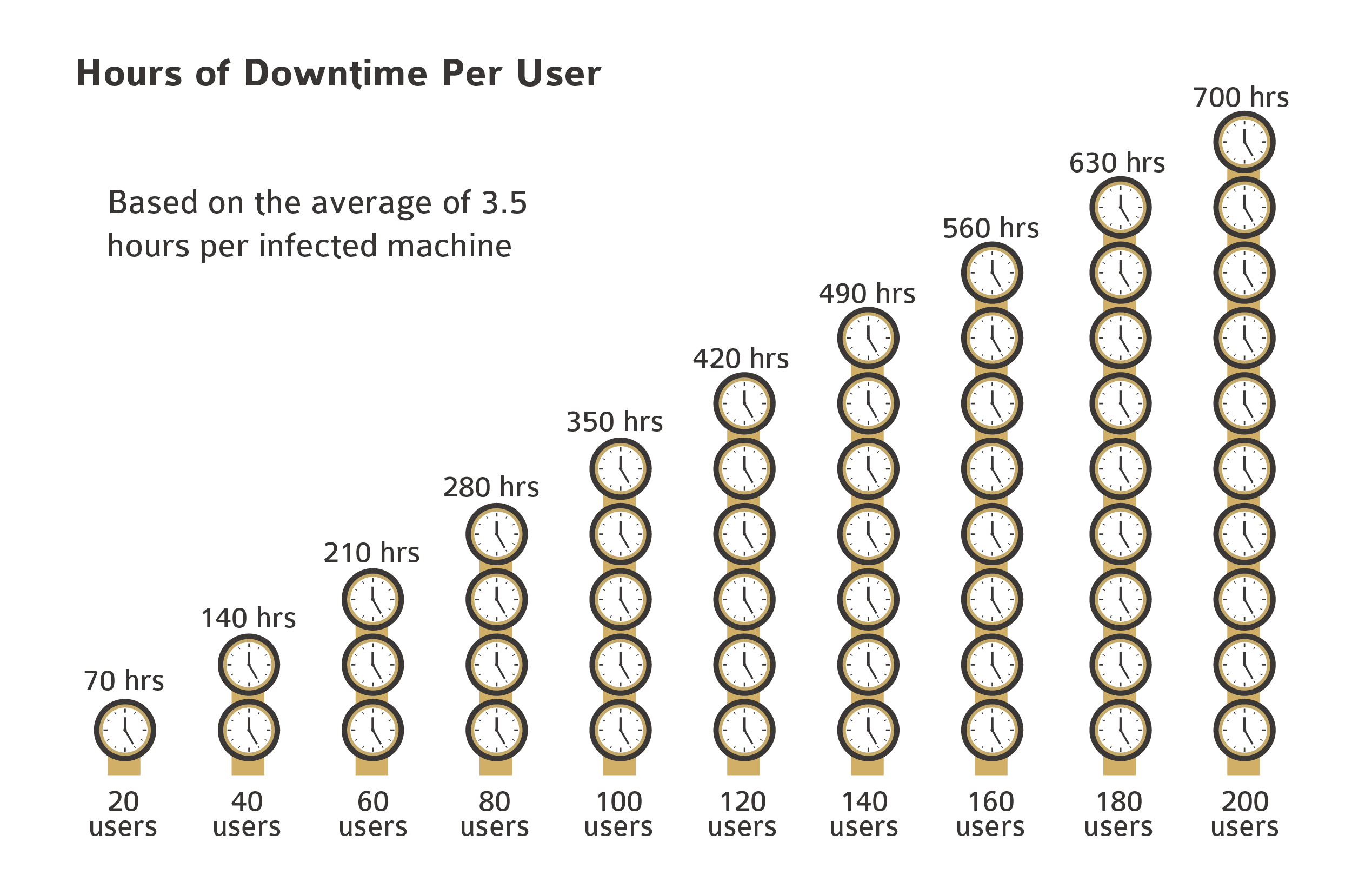
Of course, the ransom isn’t the only cost associated with a ransomware attack. Downtime for businesses that are attacked with ransomware can last from a few hours up to a week, with the potential to significantly impact your business. Recovery of data on ransomware infected machines can average 3.5 hours. On a network with 100 users, restoring your data could take up to 350 hours, even using industry standard backup protocols.
Defending Against Ransomware
It’s clear ransomware attacks are costly to your business. It’s also clear that there are multiple reasons why these attacks succeed. That’s why businesses must adopt a multi-layered approach to solving the problem. There’s no silver bullet – you must look at all the different ways that your business may be vulnerable and address them.
There are two approaches to protect your business: increased network security and improved security and backup practices at the business level, and managing the user practices that can make your business vulnerable. In our next post, we’ll discuss those user practices. Here, we’ll discuss the business level approaches that can help safeguard your networks and data.
Seven Ways to Protect Your Business From Ransomware
- Use a Network Attached Storage (NAS) device. Ransomware spreads at lightning speed from the point of entry, affecting your entire network and every device on it within minutes. Moving data from one server or disc to another takes precious time you just don’t have, so the ability to disconnect your storage from the network is critical. We recommend that all clients invest in a Network Attached Storage (NAS) device to keep their data safe. A NAS device is a backup drive that is intended to be disconnected from the network when disaster strikes. The best ones come with automated versioning so you can easily install the most recent backup in case of an attack.
- Take a layered approach to backups. In addition to a NAS device, your data should be stored in multiple locations. A rule of thumb in the security industry is “3 – 2 – 1”: three backup copies on two media, including one stored offsite. Cloud storage as part of a layered backup strategy that incorporates NAS devices meets these criteria; it’s the best way to keep your data safe.
- Apply updates and patches. When a new ransomware variant is released, software manufacturers get right to work developing updates and patches to combat them. That’s why it’s so important to apply patches and fixes as soon as possible after they are released. At Tolar Systems, this is part of the service we provide.
- Layered security. Data storage isn’t the only aspect of your network where a layered approach is required. Security, too, should be layered, with advanced security in place not just at the network level, but also at the web and email gateway, physical or cloud server level, across the network and at each endpoint. This best practice is the Tolar Systems approach.
- Segmentation. Another approach for keeping networks safe is to segment your network – break it up into smaller networks that make it more difficult for ransomware to spread to larger groups of users.
- User training. Because the vast majority of ransomware attacks will enter your network through a user’s email, user training is critical. Users must understand their role in preventing these and other types of cyber-attacks.
- Disaster recovery planning. Every business should have a disaster recovery/business continuity plan in place. Ransomware is more likely to affect your business than a fire, tornado or other natural disaster, so you must have a plan to manage this risk. That way, when a ransomware attack occurs, your team can swiftly take action to protect your essential data.
Here at Tolar Systems, we’re intensifying our efforts to help our clients stay safe from ransomware attacks. All of our Complete Care clients have access to a VCIO (virtual CIO) who can help create and update an effective disaster recovery plan. Routine, timely updates and patches; layered security that protects your network, email and data storage; and segmentation when appropriate are all part of the service we provide to our Complete Care customers.
Get Started With Ransomware Protection
Tolar Systems Complete Care provides a multi-pronged approach to managing your organization’s ransomware risk. Contact us today to learn more.
Read Part 3 in our ransomware series!